
Split Email Setup: Use Microsoft 365 and Hostinger on the Same Domain
December 10, 2025Fake WhatsApp API on npm Steals Messages, Contacts, and Login Tokens
A malicious package discovered on the NPM registry is quietly abusing developer trust by pretending to be a legitimate WhatsApp Web API library. While it appears to function like a normal WhatsApp integration tool, the package secretly intercepts messages, collects contacts, and gains control of user accounts by capturing login tokens.
The package, called “lotusbail,” is disguised as a fork of the widely used @whiskeysockets/baileys library, making it look safe at first glance. What makes this threat especially dangerous is that it actually works as advertised.
Developers can send and receive WhatsApp messages using the API, but in the background, the package links an attacker’s device to the victim’s WhatsApp account, giving full access to conversations and sensitive data. With more than 56,000 downloads, this malicious NPM package highlights a growing risk in software supply chains where even functional libraries can hide serious security threats.
It can pass code reviews and be delivered to production systems without generating any red flags thanks to this ingenious strategy. Developers install it, test it, and see that it functions, but they are unaware of the theft taking place in the background.
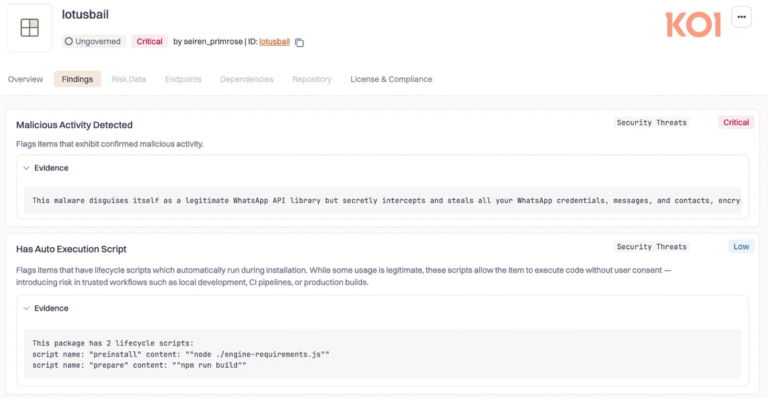
Researchers at supply-chain security firm Koi Security have flagged a malicious NPM package called “lotusbail” that targets developers building WhatsApp integrations.
Koi says the package can steal WhatsApp authentication tokens and session keys, copy messages in and out, and exfiltrate contacts, media, and documents. It masquerades as a working tool, but quietly siphons data during normal authentication and messaging flows.
How the Malicious WhatsApp Package Steals Credentials in Plain Sight
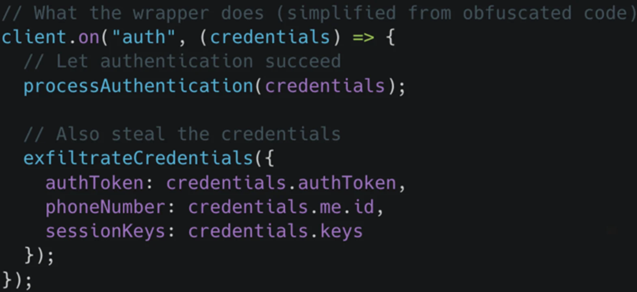
Koi’s analysis suggests the malware wraps a legitimate WebSocket client used to talk to WhatsApp. That wrapper acts like a hidden checkpoint. It sees everything before your app does.
- When you authenticate, it captures tokens and session keys
- When messages arrive, it intercepts and records them
- When you send messages, it duplicates and logs them
- It then packages up contacts, files, and chat history for exfiltration
Koi notes the approach resembles @whiskeysockets/baileys, a popular TypeScript library for WhatsApp Web integrations. That familiarity can make the malicious package look trustworthy at a glance.
WhatsApp already encrypts messages end-to-end. If a third-party library adds extra encryption for outbound traffic, it can be a sign it’s hiding stolen data, not protecting users.
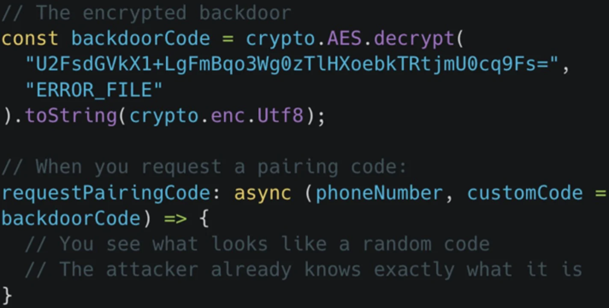
The most serious behaviour is persistence. Koi says the package includes functionality that can link the attacker’s device to the victim’s WhatsApp account through the device pairing process.
That matters because access can remain even after the package is removed. The attacker may stay connected until the victim manually removes linked devices inside WhatsApp settings.
Stealth and anti-analysis tricks
To reduce detection, Koi reports multiple layers of obfuscation and anti-debugging:
- Outbound exfiltration is hidden behind layered encoding and encryption
- Stolen data is encrypted before it’s sent to an attacker-controlled endpoint
- The code reportedly uses multiple “infinite loop” traps that trigger when debugging is detected
Koi also highlighted an important red flag: the package adds extra encryption for outbound data, even though WhatsApp messaging already uses end-to-end encryption. In this context, that extra crypto likely exists to hide theft, not to protect users.
The disclosure follows separate reporting from ReversingLabs on malicious NuGet packages impersonating crypto and blockchain tooling. Those samples reportedly aim to redirect transactions or steal secrets such as keys and seed phrases.
Mitigation
- Remove lotusbail from your project and rebuild from a known-clean state.
- Check WhatsApp → Linked devices and remove anything you don’t recognise.
- Rotate credentials and tokens used by the integration, where possible.
- Review logs for unusual authentication events and new device pairings.
- Monitor runtime behaviour for unexpected outbound connections during login flows.
- Pin dependency versions, use lockfiles, and enable automated supply-chain scanning.
- Treat “looked fine in source” as insufficient; validate packages by behaviour at runtime.
I provide cybersecurity and infrastructure services: cloud/hybrid setup, hardening, and secure self-hosted deployments (Docker/virtualisation), plus Jira/Confluence administration. For consulting or managed support, visit my Contact page.







