
How to Install Ubuntu VM in Proxmox: A Beginner’s Guide
August 10, 2025
Choosing Your Perfect Pocket Companion: A 2025 Smartphone Buyer’s Guide
August 11, 2025Google Becomes Latest Victim in Massive Salesforce Data Breach
Google has confirmed a data breach involving one of its Salesforce CRM instances, affecting the contact details of potential Google Ads customers. The tech giant began notifying affected users on 8 August 2025, following the incident.
The breach, disclosed publicly on 5 August 2025, was linked to the cybercriminal group ShinyHunters (UNC6040), who compromised the system in June 2025. Exposed information includes business names, phone numbers, and sales-related notes, primarily for small and medium-sized businesses.
In its notification, Google stated:
We’re writing to let you know about an event that affected a limited set of data in one of Google’s corporate Salesforce instances used to communicate with prospective Ads customers.
Exposed data included business names, phone numbers, and sales notes, primarily for small and medium-sized businesses. Google stressed that no payment information was compromised and that Google Ads accounts, Merchant Center, Google Analytics, and other Ads products were unaffected.
The cyberattack was carried out using advanced voice phishing (vishing) techniques. Threat actors posed as IT support staff to trick employees into granting system access. Google confirmed that payment data was not exposed and that Google Ads Account, Merchant Center, Google Analytics, and other Ads products were unaffected.
Instead of exploiting a technical flaw in Salesforce, the attackers used social engineering, exploiting human trust. The stolen data included business names, phone numbers, and “related notes” used by Google sales agents for follow-up.
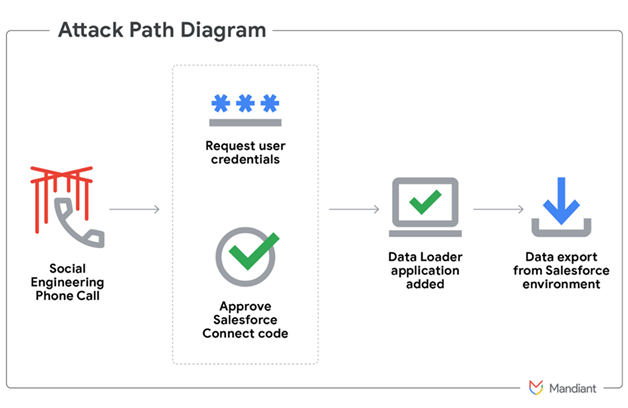
Google’s investigation found the breach occurred through a malicious version of Salesforce’s Data Loader. During fraudulent calls, employees were persuaded to authorise what appeared to be a legitimate connected app, unknowingly giving cybercriminals extensive access to extract data. The company described the stolen information as “basic and largely public business details”.
The attack was attributed to ShinyHunters, a group linked to multiple Salesforce breaches. They claim to have stolen about 2.55 million data records, though the number of unique records is unclear. ShinyHunters also claim collaboration with Scattered Spider, the group allegedly responsible for the initial system access.
ShinyHunters claimed:
Like we have said repeatedly already, ShinyHunters and Scattered Spider are one and the same. They provide us with initial access and we conduct the dump and exfiltration of the Salesforce CRM instances. Just like we did with Snowflake.
Google Confirms Cyberattack Linked to “Sp1d3rHunters”
Cybercriminals calling themselves “Sp1d3rHunters” have been linked to a targeted cyberattack against Google. The name reflects the overlapping individuals involved in these breaches.
Google began notifying affected users in early August, completing email alerts by 8 August 2025. According to the Google Threat Intelligence Group (GTIG), hacking group UNC6040 carried out the intrusions, while UNC6240 handled extortion, demanding Bitcoin payments within 72 hours.
Researchers warn that the attackers have updated their hacking tools and may be preparing to launch a Data Leak Site (DLS) to publicly expose stolen information.
It was confirmed that payment details remain secure and services such as Google Ads, Merchant Center, and Google Analytics were not affected.
Part of a Larger Campaign by ShinyHunters
This attack is part of a wider campaign by ShinyHunters, a cybercriminal group targeting high-profile companies in 2025. Victims include Cisco, Qantas, LVMH brands (Louis Vuitton, Dior, Tiffany & Co.), Adidas, and Allianz Life.
The group often uses social engineering attacks to gain access to corporate credentials. In some cases, employees are tricked into linking a malicious version of Salesforce’s Data Loader OAuth app to their company’s Salesforce environment.
How the Attack Works
Once access is secured, the attackers download entire Salesforce databases and issue ransom demands via email, threatening to leak the stolen data if payment is not made.
ShinyHunters is known for its delayed extortion model, demanding ransom months after the initial theft. They often claim affiliation with other well-known hacking collectives to increase pressure.
The hackers reportedly demanded 20 Bitcoins (around $2.3 million), later stating it was “for the lulz” rather than a serious ransom request.
The threat remains ongoing. In July, Chanel confirmed a data breach affecting US customers, caused by a compromise in a third-party Salesforce database.
Response and Security Advice
Apply strict access controls to prevent similar social engineering attacks
Google stressed the breach was contained quickly. Actions taken included:
- Terminating attacker access immediately.
- Conducting a full impact assessment.
- Adding extra security measures.
- Beginning customer notifications.
GTIG first reported these Salesforce-targeted attacks in June, with Google itself falling victim in July. The company says it took immediate action to secure systems and notify all affected users.
It was also advised businesses to:
- Strengthen employee security awareness training
- Enable multi-factor authentication
- Apply strict access controls to prevent similar social engineering attacks







